I remember all the insanely complicated things in my studies but forget the little stupid things. This is going to be a quick compile of my CCIE notes for VLAN’s
A VLAN is a Layer 2 technology that shrinks the broadcast domain in your inter-network. If there were no VLANs, depending on the size of your network, it could be brought down with a simple broadcast storm. There are two different VLAN ranges:
- Standard VLAN Range:1-1005
- Extended VLAN Range:1006-4094
If you want to use Extended VLANs, your switches must be set up in VTP Transparent mode. Also, VLANs in the extended range are not stored in the VLAN.DAT file but only in the running configuration.
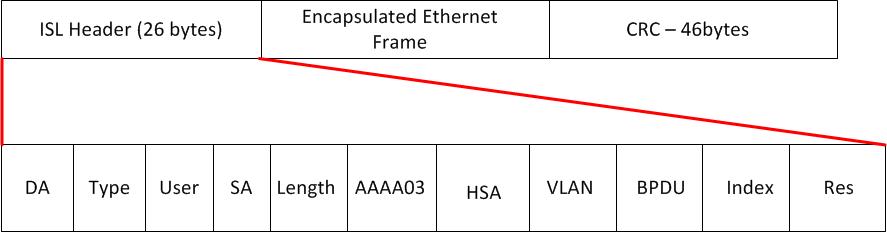
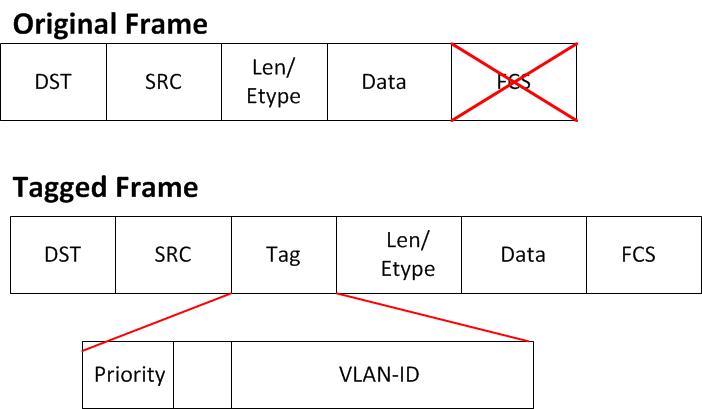
Two types of VLAN trunking Cisco switches support are ISL and 802.1Q. Below is a table of their features
| Feature | ISL | 802.1Q |
| VLANs Supported | Normal and Extended | Normal and Extended |
| Protocol Defined By | Cisco | IEEE |
| Encapsulation | Entire Frame | Inserts a .1Q Tag into the Frame |
| Supports Native VLAN | No | Yes |
ISL Frame
Dot1Q Frame
You can form a trunk between two Cisco switches in many different combinations. The ways are
| Always trunk on this end. DO NOT send DTP messages | Definition | Will Trunk With |
| Switchport mode trunk (on) | Always trunk on this end, and send DTP messages | On, desirable, auto |
| Switchport mode trunkSwitchport nonegotiate | Always trunk on this end DO NOT send DTP messages | On |
| Switchport mode dynamic desirable | Send DTP messages, and if successful, form trunk | On, desirable, auto |
| Switchport mode dynamic auto | Reply to DTP messages, and if successful, form trunk | On, desirable |
| Switchport mode access | Never trunk, BUT send out DTP messages so the other side can see the same | No one |
| Switchport mode access switch port nonegotiate | Never trunk and never send DTP messages | No one |
Configuring VLANs and 802.1Q trunking
In this example, we will look at one side of the switch; it will be set to On and allow only specific VLANs to cross it. Since it is a dot1q trunk, we are going to set the native VLAN also.
SW1(config)#int range ethernet 0/0 - 3
SW1(config-if-range)#switchport trunk encapsulation dot1q
SW1(config-if-range)#switchport mode trunk
SW1(config-if-range)#switchport trunk allowed vlan 2-5,9-10,444
SW1(config-if-range)#switchport trunk native vlan 10
SW1(config-if-range)#end
SW1#show interfaces trunk
Port Mode Encapsulation Status Native vlan
Et0/0 on 802.1q trunking 10
Et0/2 on 802.1q trunking 10
Et0/3 on 802.1q trunking 10
Port Vlans allowed on trunk
Et0/0 2-5,9-10,444
Et0/2 2-5,9-10,444
Et0/3 2-5,9-10,444
Port Vlans allowed and active in management domain
Et0/0 10
Et0/2 10
Et0/3 10
Port Vlans in spanning tree forwarding state and not pruned
Et0/0 10
Et0/2 10
Et0/3 10
SW1#Let’s say you want to add another VLAN to the trunk, and you would think all you have to do is type in switchport trunk allowed VLAN <VLAN_ID>, right?
SW1(config)#int eth0/1
SW1(config-if)#switchport trunk allowed vlan 555
SW1(config-if)#exit
SW1(config)#exit
SW1#show interfaces trunk
Port Mode Encapsulation Status Native vlan
Et0/0 on 802.1q trunking 10
Et0/2 on 802.1q trunking 10
Et0/3 on 802.1q trunking 10
Port Vlans allowed on trunk
Et0/0 2-5,9-10,444
Et0/2 2-5,9-10,444
Et0/3 2-5,9-10,444
Port Vlans allowed and active in management domain
Et0/0 10
Et0/2 10
Et0/3 10
Port Vlans in spanning tree forwarding state and not pruned
Et0/0 10
Et0/2 10
Et0/3 10Look at what happened; it removed all our VLAN configurations and only added one VLAN we wanted to add. The proper way to accomplish a task like this is to use the command switchport trunk allowed VLAN add <VLAN_ID>
SW1(config)#int eth0/1
SW1(config-if)#switchport trunk allowed vlan 2-5,9-10,444
SW1(config-if)#switchport trunk all vlan add 555
SW1(config-if)#end
SW1#show int trunk
Port Mode Encapsulation Status Native vlan
Et0/0 on 802.1q trunking 10
Et0/1 on 802.1q trunking 10
Et0/2 on 802.1q trunking 10
Et0/3 on 802.1q trunking 10
Port Vlans allowed on trunk
Et0/0 2-5,9-10,444
Et0/1 2-5,9-10,444,555
Et0/2 2-5,9-10,444
Et0/3 2-5,9-10,444
Port Vlans allowed and active in management domain
Et0/0 10
Et0/1 10
Et0/2 10
Et0/3 10
Port Vlans in spanning tree forwarding state and not pruned
Et0/0 10
Et0/1 10
Et0/2 10We are faced with three lines that seem weird when you first look at them because mostly all of the VLANs are repeated, so why have three lines? Each line means something different.
- VLANs allowed on trunk: These are VLANs you expressly permit via the trunk-allowed VLAN commands.
- VLANs allowed and active in the management domain: These are VLANs that are allowed over a trunk and exist in the VLAN configuration of the switch.
- VLANs in spanning tree forwarding state and not pruned: This is a combination of the other two, plus the pruning comes into play here. If you enable VTP pruning, it will take any VLAN that is allowed on a trunk, and if it is not explicitly assigned to an interface, it will not pass over the trunk to the switch; as you can tell, the only VLAN not assigned to an interface is VLAN 555
Being on VLAN configuration and storage, the IOS looks at VLANs when in VTP server and VTP transparent mode.
|
Function |
When in VTP Server Mode |
When in VTP Transparent Mode |
|
Normal-Range VLANs can be configured from |
Both VLAN database and configuration mode |
Both VLAN database and configuration mode |
|
Extended-Range VLANs can be configured from |
Nowhere, extended-range VLANs are only able to be configured in transparent mode. |
Configuration mode only |
|
VTP and Normal-Range VLAN configuration commands are stored in |
VLAN.Dat in flash |
Both VLAN.dat and running configuration |
|
Extended-Range VLAN configuration commands stored in |
Nowhere, extended-range VLANs are only able to be configured in transparent mode |
Running Configuration only |
The final topic I am going to cover is 802.1Q-in-Q Tunneling.
Q-in-Q tunneling is used to achieve a simple layer 2 VPN between sites via a service provider by encapsulating the customer 802.1Q frame inside a service provider 802.1Q frame. The MTU must be set to 1504 because of the additional 4-bytes from the service provider .1Q frame. The below depicts how the frame will flow from the customer’s site in NYC through the service provider to the customer’s site in Jacksonville
802.1Q-in-Q tunneling supports the following layer 2 protocols
- CDP
- PaGP
- UDLD
- VTP
It does not, however, support
- Private VLANs
- Voice VLANs