When dealing with IP services, you deal with service elements of the IP protocol carried on the IP datagram stream. Some of the IP services we are looking at;
- RARP
- ARP
- Proxy ARP
- BOOTP
- DHCP
- HSRP
- GLBP
- VRRP
- SNMP
- WCCP
- IP SLA
- NetFlow
- Router IP Traffic Export (RIPE)
- Cisco IOS Embedded Event Manager (EEM)
- Remote Monitoring (RMON)
ARP
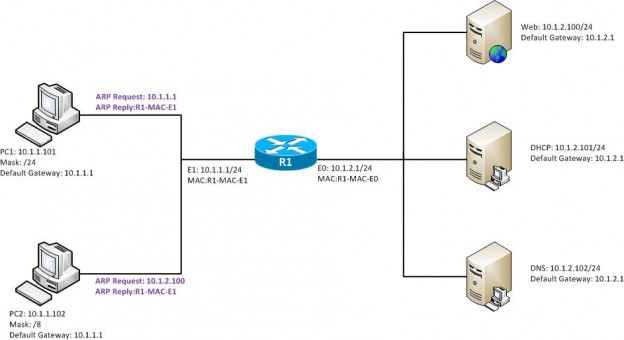
We are first going to look at ARP. ARP maps IP addresses to MAC addresses. Before a host can send data, it must do an ARP look-up to see the MAC address of the receiving (destination) device. Without ARP, packets would not flow over a network because frames are encapsulated and sent in the data-link layer. The ARP Ethernet protocol type is 0x0806, while the IP Ethernet Protocol type is 0x800. Proxy ARP: Uses the same ARP message, but the ARP request requests a host/device, not that local subnet. The router will “proxy” the ARP message from the source to the destination. An example would be The above, which shows PC2 has a subnet mask of 255.0.0.0, while the servers have a subnet mask of /24. PC2 thinks he is on the same subnet as the servers, so when he sends an ARP request, instead of putting R1 as the target, he puts the target as one of the servers. The router sees this and will proxy his ARP to the server. This is enabled by default on all Cisco routers and can be disabled with the interface command,
R1(config)#interface serial0/0
R1(config-if)#no ip proxy-arpThe next group we will look at is ways that a PC can get an IP address to communicate on the network RARP Assigns IP addresses to hosts, but only if there is a MAC to IP address mapping already in the RARP server. If there is no mapping, then the device will not get an IP address. RARP will not give out default gateways, DNS, WINS, etc. BOOTP: This was designed to fix some of the issues with RARP. With BOOTP, you can dynamically assign default gateways, DNS, WINS, etc., but you still need that static MAC to IP mapping for a device to get an IP address. DHCP: Completely dynamic address leasing. DHCP servers usually reside in a central location, and routers forward LAN broadcast DHCP requests. This process is how a DHCP relay agent works. You configure the DHCP relay agent under the interface that will be forwarding requests. The command is
R1(config)#interface serial0/0
R1(config-if)#ip helper-address 1.1.1.1You can also set an IOS device to be a DHCP server. The steps for this are;
- Setup excluded addresses
- Setup DHCP pool
- Disable conflict logging or configure a DHCP database agent
R1(config)#ip dhcp excluded-address 192.168.1.1 192.168.1.10
R1(config)#ip dhcp pool TESTPOOL
R1(dhcp-config)#network 192.168.1.0 /24
R1(dhcp-config)#default-router 192.168.1.1
R1(dhcp-config)#dns-server 192.168.1.2
R1(dhcp-config)#dns-server 192.168.1.3 192.168.1.4
R1(dhcp-config)#domain-name bigcorp.net
R1(dhcp-config)#netbios-name-server 192.168.1.8
R1(dhcp-config)#exit
R1(config)#no ip dhcp conflict logging| A client can discover their mask, DNS, and download server | RARP | BOOTP | DHCP |
| Relies on a server to allocate IP addresses | Yes | Yes | Yes |
| Encapsulates messages in IP/UDP so they can be forwarded | No | Yes | Yes |
| A client can discover their own mask, DNS, and download server | No | Yes | Yes |
| Dynamic addressing from a pool of addresses | No | No | Yes |
| Allows temporary lease of IP addresses | No | No | Yes |
| Includes extensions for registering with DNS | No | No | Yes |
First Hop Redundancy Protocols
We will look at ways to prevent a single point of failure regarding your default gateways. On a Cisco router or switch, you can accomplish this in one of three ways, either using HSRP, VRRP, or GLBP
HSRP: allows multiple routers to share a VIP and MAC address so end-user hosts do not realize when a failure occurs. Some key HSRP features are;
- VIP and VMAC (Virtual MAC) active on HSRP active router
- Standby routers listen for hello’s sent from the active router (3-second hello / 10-second dead timer by default)
- The highest priority determines the active HSRP router, with preemption enabled (100 is the default value, value can be from 1-255)
- Supports interface and route tracking. You can set the device to decrement the priority if a tracked object fails
- You can have up to 255 groups per interface
- the VMAC 0000.0C07.ACXX (where XX is the group number in hex)
- VIP must be in the same subnet as SVI or interface
- supports cleartext or MD5 authentication
HSRP Configuration
We want to set up the following;
- Setup HSRP Group 10 with a VIP of 192.168.1.1
- Give HSRP group 10 a priority of 110
- Change the default timers for group 10 to 1-second hello and 4 seconds dead.
- Configure authentication on group 10, and the passphrase is PASSWORD
- Give group 10 the name of HSRP_10.
- Give group 10 the ability to preempt. If you enable preemption, if this device were to go down and come back up, it will take back the role of the active router if his priority is larger.
- On group 10, track interface FastEthernet 0/1, and if it goes down, decrement my priority by 45
R1(config)#int eth0/0
R1(config-if)#ip address 192.168.1.2 255.255.255.0
R1(config-if)#standby 10 ip 192.168.1.1
R1(config-if)#standby 10 priority 110
R1(config-if)#standby 10 timers 1 4
R1(config-if)#standby 10 authentication PASSWORD
R1(config-if)#standby 10 name HSRP_10
R1(config-if)#standby 10 preempt
R1(config-if)#standby 10 track ethernet 0/1 45Sample output from show standby brief
R1#show standby brief
P indicates configured to preempt.
|
Interface Grp Pri P State Active Standby Virtual IP
Et0/0 10 110 P Active local 192.168.1.3 192.168.1.1If you want to see everything about an HSRP group, use the command. show standby
R1#show standby
Ethernet0/0 - Group 10
State is Active
2 state changes, last state change 00:01:25
Virtual IP address is 192.168.1.1
Active virtual MAC address is 0000.0c07.ac0a
Local virtual MAC address is 0000.0c07.ac0a (v1 default)
Hello time 1 sec, hold time 4 sec
Next hello sent in 0.128 secs
Authentication text, string "PASSWORD"
Preemption enabled
Active router is local
Standby router is 192.168.1.3, priority 105 (expires in 3.168 sec)
Priority 110 (configured 110)
Group name is "HSRP_10" (cfgd)
R1#HSRP uses only one active router, and the rest are idle. To provide load balancing in HSRP, you can use a concept called MHSRP or Multiple HSRP. In MHSRP, two or more HSRP groups are configured on each HSRP LAN interface, where the configured priority will determine which HSRP group is active. MHSRP requires the different default gateways to be handed out via DHCP. HSRP is a Cisco proprietary protocol.
VRRP is an open standard protocol that differs from HSRP in the following ways;
- VRRP uses a multicast VMAC 0000.5E00.01XX
- VRRP uses the IOS tracking feature rather than its internal tracking mechanism
- Preemption is enabled by default in VRRP
- Master in VRRP = Active in HSRP
- the VRRP group IP is the interface IP of one of the VRRP routers
VRRP basic configuration (very similar to HSRP)
R1(config)#int eth0/0
R1(config-if)#vrrp 4 ip 192.168.1.1
R1(config-if)#vrrp 4 preempt
R1(config-if)#vrrp 4 priority 120VRRP show commands, also very similar to HSRP
R1#show vrrp
Ethernet0/0 - Group 4
State is Master
Virtual IP address is 192.168.1.1
Virtual MAC address is 0000.5e00.0104
Advertisement interval is 1.000 sec
Preemption enabled
Priority is 120
Master Router is 192.168.1.2 (local), priority is 120
Master Advertisement interval is 1.000 sec
Master Down interval is 3.531 secGLBP is a newer Cisco proprietary tool that adds load balancing and gateway redundancy. Hosts still point to the default gateway, but GLBP causes different hosts to send their traffic to one of up to four routers in a GLBP group. To do so, the GLBP Active Virtual Gateway (AVG) assigns each router in a group a unique VMAC in the format 0000.B400.XXYY, where XX is the GLBP group, and YY is the number. When a client ARPs for the VIP of its default gateway, the AVG will supply the MAC of one of the four routers in the group. You can have 1024 groups per interface, but only four hosts in each group.
GLBP Configuration
R1(config)#int eth0/0
R1(config-if)#glbp 4 ip 192.168.1.1
R1(config-if)#glbp 4 pri
R1(config-if)#glbp 4 priority 120
R1(config-if)#glbp 4 name TEST_GLBP
R1(config-if)#glbp 4 load-balancing ?
host-dependent Load balance equally, source MAC determines forwarder choice
round-robin Load balance equally using each forwarder in turn
weighted Load balance in proportion to forwarder weighting
<cr>
R1(config-if)#glbp 4 load-balancing round-robinGLBP Show Commands
R1#show glbp
Ethernet0/0 - Group 4
State is Active
1 state change, last state change 00:01:23
Virtual IP address is 192.168.1.1
Hello time 3 sec, hold time 10 sec
Next hello sent in 0.192 secs
Redirect time 600 sec, forwarder timeout 14400 sec
Preemption disabled
Active is local
Standby is 192.168.1.3, priority 105 (expires in 8.320 sec)
Priority 120 (configured)
Weighting 100 (default 100), thresholds: lower 1, upper 100
Load balancing: round-robin
IP redundancy name is "TEST_GLBP"
Group members:
aabb.cc00.1000 (192.168.1.2) local
aabb.cc00.2000 (192.168.1.3)
There are 2 forwarders (1 active)
Forwarder 1
State is Active
1 state change, last state change 00:01:12
MAC address is 0007.b400.0401 (default)
Owner ID is aabb.cc00.1000
Redirection enabled
Preemption enabled, min delay 30 sec
Active is local, weighting 100
Forwarder 2
State is Listen
MAC address is 0007.b400.0402 (learnt)
Owner ID is aabb.cc00.2000
Redirection enabled, 599.840 sec remaining (maximum 600 sec)
Time to live: 14399.840 sec (maximum 14400 sec)
Preemption enabled, min delay 30 sec
Active is 192.168.1.3 (primary), weighting 100 (expires in 11.296 sec)Network Time Protocol (NTP)
NTP allows routers to keep their clocks up to date. I think this is one of the most important configurations to get correct, and if you don’t and you are troubleshooting an issue, you could be chasing your tail around for hours trying to figure out exactly when something happened. Most devices are configured in client mode, meaning they get their clock from a server. IOS devices can be either servers or clients. They can also be configured in symmetric/active mode, which is a mode that routers and switches use to synchronize with another NTP host manually. NTP supports MD5 authentication.
NTP Server Configuration
R1(config)#ntp authentication-key 1 md5 password
R1(config)#ntp authenticate
R1(config)#ntp trusted-key 1
R1(config)#ntp master 5NTP Client Configuration
R1(config)#ntp authentication-key 5 md5 thisismykey
R1(config)#ntp authenticate
R1(config)#ntp trusted-key 5
R1(config)#ntp server 1.1.1.1NTP Symmetric/Active Mode Configuration
R1(config)#ntp authentication-key 16 md5 thisismykey!
R1(config)#ntp authenticate
R1(config)#ntp trusted-key 16
R1(config)#ntp server 10.10.10.10SNMP (Simple Network Management Protocol)
Sends management information to SNMP servers. There are four major functional areas to support the core function of how managers manage SNMP agents;
- Data Definition: the syntax convention for how to define the data to an agent or manager.
- MIBs: over 100 internet standards define MIBs, each for a different technology area, and conform to the appropriate SMI version.
- Protocols: the messages used by agents and managers to exchange management data
- Security and Administration: how to secure the exchange of data between agents and manager
SNMP Version Summaries
| SNMP Version | Description |
| 1 | Uses SIMv1, simple authentication with communities, but used MIB-I originally |
| 2 | Uses SIMv2, removed the requirement for communities, added GET bulk inform messages, but began with MIB-II originally |
| 2c | Features of SNMPv2, but with v1 communities |
| 3 | Identical to v2c, but adds better security and uses MIB-II |
SNMP Protocol Messages
| Message | Initial Version | Response Message | Typically Sent By | Main Purpose |
| GET | 1 | Response | Manager | Request for a single variable value |
| GET NEXT | 1 | Response | Manager | Request for the next single MIB leave variable in the MIB tree |
| GET BULK | 2 | Response | Manager | Request for multiple consecutive MIB variables with one request. Useful for getting complex structures like the IP routing table |
| RESPONSE | 1 | None | Agent | Used to respond to GET/SET messages |
| SET | 1 | Response | Manager | Sent by the manager to an agent to tell the agent to set a variable to a particular variable |
| TRAP | 1 | None | Agent | Allows an agent to send unsolicited information to the manager |
| INFORM | 2 | Response | Manager | Used between SNMP managers to allow MIB data to be exchanged |
SNMP Security
Only v3, adds authentication and encryption using MD5/SHA for each protocol message and DES for encryption.
We want to accomplish the following in an SNMP configuration
- Sends traps to 10.44.55.100
- sends traps for a variety of SNMP events
- Set optional ID, router chassis, and contact information
- R/W access to 10.44.50.0/24 via an ACL
R1(config)#access-list 1 permit 10.44.50.0 0.0.0.255
R1(config)#snmp-server community communitystringhere 1
R1(config)#snmp-server location NYC DATA-CENTER RACK LL-25
R1(config)#snmp-server contact NETWORK ENGINEERING (212) 555-1212
R1(config)#snmp-server enable traps snmp
R1(config)#snmp-server enable traps hsrp
R1(config)#snmp-server enable traps config
R1(config)#snmp-server enable traps bgp
R1(config)#snmp-server host 10.44.50.100 communitystringhereWeb Cache Communication Protocol (WCCP)
Redirects traffic to a content engine or WAN accelerator
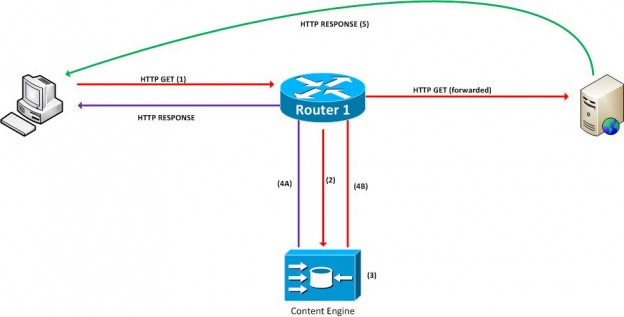
The steps taken in the above diagram are as follows;
- The client sends an HTTP request to a web server.
- Routers WCCP option notices an HTTP request and sends it to the content engine.
- The content engine looks to see if the resource is cached
- The following two things will happen:
- If an object is cached, the content engine sends an HTTP response, which includes the object back to the client.
- if an object is not cached, the content engine forwards the original HTTP GET request to the original server
- If 4B was taken, the server replies to the client without knowing that a packet was ever redirected to the content engine.
WCCP uses UDP/2048. You can cluster up to 32 content engines. In WCCPv1, the router with the lowest IP is the lead engine. WCCPv2 is the default and holds the following benefits over WCCPv1
- Supports more TCP/UDP ports
- Permits segment caching servers by protocol(s) and uses a priority system for deciding which cluster to use for a particular cached protocol.
- Supports multicast to simplify deployment
- Supports multiple routers per cluster (32) for redundancy and load distribution
- MD5 security
- Transparent error handling
You can use ACLs to tell the router what traffic to allow to the content engine and what redirected traffic to accept from the content engine.
WCCP Example (with ACL)
R1(config)#ip access-list standard ALLOW_TO_CONTENT_ENGINE
R1(config-std-nacl)#deny 192.168.1.0 0.0.0.255
R1(config-std-nacl)#deny 192.168.2.0 0.0.0.255
R1(config-std-nacl)#permit 10.10.0.0 0.0.0.255
R1(config-std-nacl)#permit 172.16.24.0 0.0.0.255
R1(config-std-nacl)#exit
R1(config)#ip access-list standard ALLOW_FROM_CONTENT_ENGINE
R1(config-std-nacl)#permit 12.44.50.0 0.0.0.7
R1(config-std-nacl)#permit 4.2.2.2 0.0.0.0
R1(config-std-nacl)#permit 8.8.8.8 0.0.0.0
R1(config-std-nacl)#permit 65.44.4.0 0.0.0.255
R1(config-std-nacl)#exit
R1(config)#int eth0/0
R1(config-if)#ip wccp web-cache redirect-list ALLOW_TO_CONTENT_ENGINE
R1(config-if)#ip wccp web-cache group-list ALLOW_FROM_CONTENT_ENGINEWCCP Example (without ACL)
R1(config)#ip wccp web-cache group-address 239.1.1.1 password cisco
R1(config)#int eth0/1
R1(config-if)#ip wccp web-cache redirect out
R1(config-if)#int eth0/0
R1(config-if)#ip wccp web-cache redirect in
R1(config-if)#IP SLA
IP SLA lets you actively probe the network to gather performance information. The IP SLA feature lets you measure the following parameters for network performance;
- Delay (one-way or round-trip)
- Jitter (directional)
- Packet loss (directional)
- Packet sequencing
- Path (per-hop)
- Connectivity (UDP Echo, TCP Connect, ICMP Echo, and ICMP Path-Echo)
- Server or website download time
- Voice quality metrics (MOS)
Implementing IP SLA (once configured and running, they cannot be modified; they must be deleted to be modified)
- Configure SLA operation type, including required options
- Configure any desired threshold conditions
- Configure responder(s) if appropriate
- Schedule or start operation and monitor results
- Review results, either in IOS CLI or SNMP
- Optionally, MD5 is the authentication method of choice, used with IP SLA key-chain.
Configuring IP SLA
R1(config)#ip sla 1
R1(config-ip-sla)#udp-echo 1.2.3.4 4322
R1(config-ip-sla-udp)#frequency 5
R1(config-ip-sla-udp)#end
R1#config t
R1(config)#ip sla schedule 1 life forever start-time nowImplementing Netflow
Netflow allows administrators to look at network traffic. The components of Netflow are;
- Record: A set of predefined and user-defined key fields for network monitoring (source/destination and IP/Port)
- Flow Monitors: Applied to an interface and include records, a cache, and optionally a flow exporter. The flow monitor cache collects information about flows.
- Flow Exporter: Export cache flow information to an outside system
- Flow Samples: Designed to reduce the load on Netflow-enabled devices. Flow samplers allow specifying the sample size of traffic Netflow analyzes to a ratio of 1:2 or 1:32768
Router IP Traffic Export (RIPE)
Exports IP packets to a VLAN or LAN interface for analysis typically used for IDS deployments (like SPAN ports, but for routers)
Implementing Cisco IOS Embedded Event Manager (EEM)
Tracks and classifies events that take place and provides notification for these events. EEM overlaps with RMON but is more powerful. EEM uses event detectors and actions to provide notification of these events. Event detectors EEM supports include;
- SNMP object monitoring
- Screening Syslog messages (using regular expressions)
- Monitoring counters
- Timers (absolute time-of-day, countdown, watchdog, CRON)
- Screening CLI input for a regular expression match
- Hardware insertion and removal
- Routing table changes
- IP SLA and Netflow events
- Generic On-Line Diagnostic (GOLD) events
Event actions that EEM provides include
- Generating prioritized Syslog messages
- Reloading the router
- Switching to a secondary processor on a redundant platform
- Generating SNMP traps
- Setting or modifying a counter
- Executing a command
- Sending a brief email message
- Requesting system information when an event occurs
- Reading or setting the state of a tracked object
Basic EEM configuration to send a Syslog message when someone types wr
R5(config)#event manager applet CLI-WR-MEM
R5(config-applet)#event cli pattern 'wr' sync yes
R5(config-applet)#action 1.0 syslog msg "$_cli_msg command executed"
R5(config-applet)#set 2.0 _exit_status 1Remote Monitoring (RMON)
Event notification, an extension of SNMP
- Alarm: what will happen if the event trips the alarm
- Event: numbered, the user-configured threshold for SNMP object