Our last post looked at Q-in-Q tunneling using one port, but what if you had to extend an EtherChannel from one data center to the other? We can also use Q-in-Q tunneling with EtherChannel. The train of thought is similar to how we did just a straight Q-in-Q tunnel, but now, with EtherChannel, we need a few more pieces to the configuration. First, we need to identify the port as a layer 2 protocol tunnel, and depending on whether we choose PAgP or LACP, we need to specify that in the configuration. Also, if you want to send any layer 2 information over it, like spanning tree or CDP, you must identify that in the layer 2 tunnel configuration. We will look at the following diagram to base our configuration.
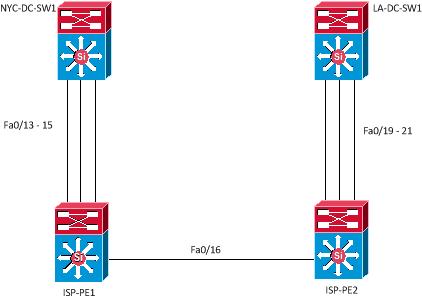
To summarize, we are going to implement the following;
* Configure an EtherChannel using PAgP between NYC-DC-SW01 and LA-DC-SW02
* Pass Spanning-tree and CDP information over the tunnel
The ISP configuration is missing the trunk configuration between ISP-PE1 and ISP-PE2. It is the same as the previous post (802.1 Q-in-Q Tunneling)
Configuration – NYC-DC-SW1
NYC-DC-SW1(config)#interface FastEthernet0/13
NYC-DC-SW1(config-if)# switchport trunk encapsulation dot1q
NYC-DC-SW1(config-if)# switchport mode trunk
NYC-DC-SW1(config-if)# channel-group 1 mode desirable
Creating a port-channel interface Port-channel 1
NYC-DC-SW1(config-if)#
NYC-DC-SW1(config-if)#interface FastEthernet0/14
NYC-DC-SW1(config-if)# switchport trunk encapsulation dot1q
NYC-DC-SW1(config-if)# switchport mode trunk
NYC-DC-SW1(config-if)# channel-group 1 mode desirable
NYC-DC-SW1(config-if)#
NYC-DC-SW1(config-if)#interface FastEthernet0/15
NYC-DC-SW1(config-if)# switchport trunk encapsulation dot1q
NYC-DC-SW1(config-if)# switchport mode trunk
NYC-DC-SW1(config-if)# channel-group 1 mode desirable
NYC-DC-SW1(config-if)#
NYC-DC-SW1(config-if)#Interface Port-Channel 1
NYC-DC-SW1(config-if)# switchport trunk encapsulation dot1q
NYC-DC-SW1(config-if)# switchport mode trunkConfiguration – ISP-PE1
ISP-PE1(config)#interface FastEthernet0/13
ISP-PE1(config-if)# switchport access vlan 100
ISP-PE1(config-if)# switchport mode dot1q-tunnel
ISP-PE1(config-if)# l2protocol-tunnel point-to-point pagp
ISP-PE1(config-if)# l2protocol-tunnel cdp
ISP-PE1(config-if)# l2protocol-tunnel stp
ISP-PE1(config-if)#
ISP-PE1(config-if)#interface FastEthernet0/14
ISP-PE1(config-if)# switchport access vlan 200
ISP-PE1(config-if)# switchport mode dot1q-tunnel
ISP-PE1(config-if)# l2protocol-tunnel point-to-point pagp
ISP-PE1(config-if)# l2protocol-tunnel cdp
ISP-PE1(config-if)# l2protocol-tunnel stp
ISP-PE1(config-if)#
ISP-PE1(config-if)#interface FastEthernet0/15
ISP-PE1(config-if)# switchport access vlan 300
ISP-PE1(config-if)# switchport mode dot1q-tunnel
ISP-PE1(config-if)# l2protocol-tunnel point-to-point pagp
ISP-PE1(config-if)# l2protocol-tunnel cdp
ISP-PE1(config-if)# l2protocol-tunnel stpConfiguration – ISP-PE2
ISP-PE2(config)#interface FastEthernet0/19
ISP-PE2(config-if)# switchport access vlan 100
ISP-PE2(config-if)# switchport mode dot1q-tunnel
ISP-PE2(config-if)# l2protocol-tunnel point-to-point pagp
ISP-PE2(config-if)# l2protocol-tunnel cdp
ISP-PE2(config-if)# l2protocol-tunnel stp
ISP-PE2(config-if)#
ISP-PE2(config-if)#interface FastEthernet0/20
ISP-PE2(config-if)# switchport access vlan 200
ISP-PE2(config-if)# switchport mode dot1q-tunnel
ISP-PE2(config-if)# l2protocol-tunnel point-to-point pagp
ISP-PE2(config-if)# l2protocol-tunnel cdp
ISP-PE2(config-if)# l2protocol-tunnel stp
ISP-PE2(config-if)#
ISP-PE2(config-if)#interface FastEthernet0/21
ISP-PE2(config-if)# switchport access vlan 300
ISP-PE2(config-if)# switchport mode dot1q-tunnel
ISP-PE2(config-if)# l2protocol-tunnel point-to-point pagp
ISP-PE2(config-if)# l2protocol-tunnel cdp
ISP-PE2(config-if)# l2protocol-tunnel stpConfiguration – LA-DC-SW1
LA-DC-SW1(config)#interface FastEthernet0/19
LA-DC-SW1(config-if)# switchport trunk encapsulation dot1q
LA-DC-SW1(config-if)# switchport mode trunk
LA-DC-SW1(config-if)# channel-group 2 mode desirable
Creating a port-channel interface Port-channel 2
LA-DC-SW1(config-if)#
LA-DC-SW1(config-if)#interface FastEthernet0/20
LA-DC-SW1(config-if)# switchport trunk encapsulation dot1q
LA-DC-SW1(config-if)# switchport mode trunk
LA-DC-SW1(config-if)# channel-group 2 mode desirable
LA-DC-SW1(config-if)#
LA-DC-SW1(config-if)#interface FastEthernet0/21
LA-DC-SW1(config-if)# switchport trunk encapsulation dot1q
LA-DC-SW1(config-if)# switchport mode trunk
LA-DC-SW1(config-if)# channel-group 2 mode desirable
LA-DC-SW1(config-if)#
LA-DC-SW1(config-if)#
LA-DC-SW1(config-if)#
LA-DC-SW1(config-if)#
LA-DC-SW1(config-if)#Interface Port-Channel 2
LA-DC-SW1(config-if)#switchport trunk encapsulation dot1q
LA-DC-SW1(config-if)#switchport mode trunkAs you can tell, all the actual configuration is done on the provider devices. As the customers, we need to make sure we have our EtherChannel configured correctly and that we know how the service provider has the l2protocol-tunnel setup. If there is a mismatch there, then the configuration will not work.
There are a few tools you can use to verify that this is working properly
Verify
- Show CDP Neighbors, you should see only NYC-DC-SW01 and LA-DC-SW01, respectively (you should not see any Service Provider devices; you will see CDP devices inside your network if there are any)
# LA-DC-SW1 CDP Neighbors
LA-DC-SW1#show cdp neighbors
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone,
D - Remote, C - CVTA, M - Two-port Mac Relay
Device ID Local Intrfce Holdtme Capability Platform Port ID
NYC-DC-SW1 Fas 0/21 132 S I WS-C3550- Fas 0/15
NYC-DC-SW1 Fas 0/20 132 S I WS-C3550- Fas 0/14
NYC-DC-SW1 Fas 0/19 103 S I WS-C3550- Fas 0/13
# NYC-DC-SW1 CDP Neighbors
NYC-DC-SW1#show cdp neighbor
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone
Device ID Local Intrfce Holdtme Capability Platform Port ID
LA-DC-SW1 Fas 0/15 131 S I WS-C3560- Fas 0/21
LA-DC-SW1 Fas 0/14 131 S I WS-C3560- Fas 0/20
LA-DC-SW1 Fas 0/13 101 S I WS-C3560- Fas 0/192. Show Interfaces Trunk
# NYC-DC-SW1 - Show interface trunk
NYC-DC-SW1#show interface trunk
Port Mode Encapsulation Status Native vlan
Po1 on 802.1q trunking 1
Port Vlans allowed on trunk
Po1 1-4094
Port Vlans allowed and active in management domain
Po1 1,100,146,456
Port Vlans in spanning tree forwarding state and not pruned
Po1 1,100,146,456
# LA-DC-SW1 - Show interface trunk
LA-DC-SW1#show interface trunk
Port Mode Encapsulation Status Native vlan
Po2 on 802.1q trunking 1
Port Vlans allowed on trunk
Po2 1-4094
Port Vlans allowed and active in management domain
Po2 1,100,146,200,300,456
Port Vlans in spanning tree forwarding state and not pruned
Po2 1,100,146,200,300,4563. show EtherChannel Summary – You should see your peer and it should look similar to the below (your output may vary depending on your port-channel interface numbers and any other port channels you have configured
# NYC-DC-SW1 - show etherchannel summary
NYC-DC-SW1#show etherchannel summary
Flags: D - down P - bundled in port-channel
I - stand-alone s - suspended
H - Hot-standby (LACP only)
R - Layer3 S - Layer2
U - in use f - failed to allocate aggregator
M - not in use, minimum links not met
u - unsuitable for bundling
w - waiting to be aggregated
d - default portNumber of channel-groups in use: 1
Number of aggregators: 2
Group Port-channel Protocol Ports
------+-------------+-----------+-----------------------------------------------
1 Po1(SU) PAgP Fa0/13(P) Fa0/14(P) Fa0/15(P)
# LA-DC-SW1 - show etherchannel summary
LA-DC-SW1#show etherchannel summary
Flags: D - down P - bundled in port-channel
I - stand-alone s - suspended
H - Hot-standby (LACP only)
R - Layer3 S - Layer2
U - in use f - failed to allocate aggregator
M - not in use, minimum links not met
u - unsuitable for bundling
w - waiting to be aggregated
d - default portNumber of channel-groups in use: 1
Number of aggregators: 1
Group Port-channel Protocol Ports
------+-------------+-----------+-----------------------------------------------
2 Po2(SU) PAgP Fa0/19(P) Fa0/20(P) Fa0/21(P)The final test would be to issue a ping from one end to the other, which will be successful.