So blogging world, it has been a while since my last post. Since my last post, I paid RTP another visit and did not leave with the prize; although my scores significantly increased, it still was not enough to get that coveted 5-digit number.
Today, we will look at the lock and key access-lists and why they would be helpful. People can argue and say, Mike, why would you want to deploy a lock and key solution when all you need to do is just put a firewall in the path and only allow specific subnets access to the resources behind it, or for that matter, just an ACL on the interface facing the protected network. I agree with that statement, but let’s face it: firewalls are expensive, especially for a small business, and redesigning your infrastructure to have a segregated network may not always be the right move. That is where the lock and key ACLs come in.
A lock and key ACL is a dynamic access list that could match a specific ACL string (permit TCP any host 172.20.44.24 eq telnet) or a broad ACL string (permit TCP any 172.20.44.0 0.0.0.255). The key here is using the key dynamic in the access-list. I will show two requirements that need to be met in two scenarios to show the lock’s and key ACL’s flexibility. The diagram will be the same and looks like this.
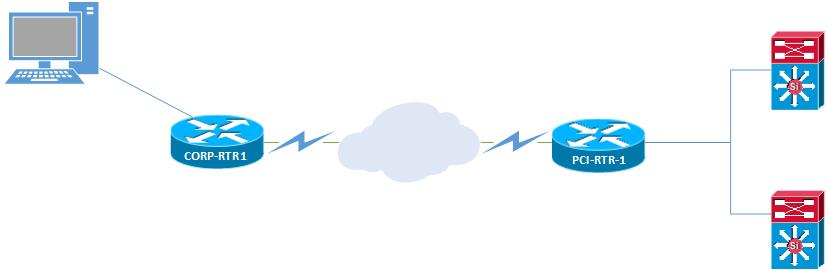
So, in the above diagram, we have four network devices: CORP-RTR1 is a device that anyone can access, and PCI-RTR-1 is a device on the edge of our protected PCI environment. We are tasked with configuring.
Only permit telnet access to the PCI management network (172.26.45.0/24). This access should only be granted upon successful login with the username PCI with a password of admin.
How would we go about doing this?
The configuration is going to be all done on PCI-RTR-1. The first step is to create the username and password.
Configuration
Username and password
PCI-RTR-1(config)#username PCI password admin
Define Access-lists
Next, we define our access-list. We only want to permit telnet access to the PCI environment, so let’s only allow telnet to the serial interface of PCI-RTR-1 so we can establish the connection, then deny telnet to all other IPs on that router and put in our dynamic ACL line.
PCI-RTR-1(config)#ip access-list extended LOCKANDKEY
PCI-RTR-1(config-ext-nacl)#permit tcp any host 172.16.25.5 eq telnet
PCI-RTR-1(config-ext-nacl)#deny tcp any host 172.24.24.50 eq telnet
PCI-RTR-1(config-ext-nacl)#dynamic PCI-ACCESS permit tcp any 172.26.45.0 0.0.0.255 eq telnet
PCI-RTR-1(config-ext-nacl)#deny tcp any 172.26.45.0 0.0.0.255 eq telnet
PCI-RTR-1(config-ext-nacl)#permit ip any anyApply the access-list to the Interface
We apply the lock and key ACL to the interface and add the following to the user account.
PCI-RTR-1(config)#int s0/2/0
PCI-RTR-1(config-if)#ip access
PCI-RTR-1(config-if)#ip access-group LOCKANDKEY in
PCI-RTR-1(config)#username PCI autocommand access-enable host
PCI-RTR-1(config)#line vty 0 4
PCI-RTR-1(config-line)#login localTesting
Now, if from PC1 we try to telnet to PCI-ACCESS-01(172.26.45.55), we should get an error saying the host is unreachable.
PC1#telnet 172.26.45.55
Trying 172.26.45.55 ...
% Destination unreachable; gateway or host downNow let’s try to log in to PCI-RTR-1 and try to access PCI-ACCESS-01 again, this is due to the mechanisms of how lock and key access-lists work. There needs to be interesting traffic to “unlock” the ACL before traffic can flow.
PC1#telnet 172.16.25.5
Trying 172.16.25.5 ... Open
User Access Verification
Username: PCI
Password:
[Connection to 172.16.25.5 closed by foreign host]
PC1#telnet 172.26.45.55
Trying 172.26.45.55 ... Open
PCI-ACCESS-01#enable
Password:
PCI-ACCESS-01#who
Line Host(s) Idle Location
1 vty 00:00:00 10.20.55.24Verification
Ok, we have access; now that we have access, let us look at the ACL on PCI-RTR-1 and see if it changed.
PCI-RTR-1#sh access-list
Extended IP access list LOCKANDKEY
10 permit tcp any host 172.16.25.5 eq telnet (25 matches)
20 deny tcp any host 172.24.24.50 eq telnet
30 Dynamic PCI-ACCESS permit tcp any 172.26.45.0 0.0.0.255 eq telnet
permit tcp host 10.20.55.24 172.26.45.0 0.0.0.255 eq telnet (34 matches)
40 deny tcp any 172.26.45.0 0.0.0.255 eq telnet (3 matches)
50 permit ip any any (27 matches)Changing Lock and Key Access-List
Look at that; it dynamically punched a hole in the ACL for us. Now, this only controls telnet access, nothing else. I don’t need to log in to PCI-RTR-1 to ping, and the dynamic access-list only wants to see a login for telnet. So, let’s change the ACL up. Let’s say for any IP connection, you must log in. We will make an exception for SNMP, as we utilize ACLs on the PCI devices. The configuration stays the same except for the access-list, which looks like this.
PCI-RTR-1(config)#ip access-list extended LOCKANDKEY
PCI-RTR-1(config-ext-nacl)#permit tcp any host 172.16.25.5 eq telnet
PCI-RTR-1(config-ext-nacl)#deny tcp any host 172.24.24.50 eq telnet
PCI-RTR-1(config-ext-nacl)#dynamic PCI-ACCESS permit ip any 172.26.45.0 0.0.0.255
PCI-RTR-1(config-ext-nacl)#deny ip any 172.26.45.0 0.0.0.255
PCI-RTR-1(config-ext-nacl)#permit ip any anyRe-Verify
Now let us try to ping PCI-ACCESS-01(172.26.45.55)
PC1#ping 172.26.45.55
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.26.45.55, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)What could the problem be?
ICMP: dst (10.20.55.24) administratively prohibited unreachable rcv from 172.16.25.5
This tells me that it is hitting we deny IP any any, which is what we want to see. Let’s see if we can telnet to PCI-ACCESS-01(172.26.45.55) on port 80
PC1#debug ip tcp packet port 80
TCP Packet debugging is on for port number 80
PC1#telnet 172.26.45.55 80
Trying 172.26.45.55, 80 ...
% Destination unreachable; gateway or host down
PC1#
tcp0: O CLOSED 172.26.45.55:80 10.20.55.24:51106 seq 2196117134
OPTS 4 SYN WIN 4128
TCP: sent RST to 172.26.45.55:23 from 10.20.55.24:17431Check with Telnet
This is what we want to see. The connection is closed immediately. Telnet to PCI-RTR-1 and authenticate to try these tests again.
PC1#telnet 172.16.25.5
Trying 172.16.25.5 ... Open
User Access Verification
Username: PCI
Password:
[Connection to 172.16.25.5 closed by foreign host]
PC1#ping 172.26.45.55 rep 4
Type escape sequence to abort.
Sending 4, 100-byte ICMP Echos to 172.26.45.55, timeout is 2 seconds:
!!!!
Success rate is 100 percent (4/4), round-trip min/avg/max = 28/28/28 ms
PC1#telnet 172.26.45.55 80
Trying 172.26.45.55, 80 ... Open
GET /
WWW-Authenticate: Basic realm="level_15_access"
401 Unauthorized
[Connection to 172.26.45.55 closed by foreign host]And we have success; now let’s check the access-list
PCI-RTR-1#sh access-list
Extended IP access list LOCKANDKEY
10 permit tcp any host 172.16.25.5 eq telnet (25 matches)
20 deny tcp any host 172.24.24.50 eq telnet
30 Dynamic PCI-ACCESS permit ip any 172.26.45.0 0.0.0.255
permit ip host 10.20.55.24 172.26.45.0 0.0.0.255 (56 matches)
40 deny ip any 172.26.45.0 0.0.0.255 (102 matches)
50 permit ip any any (42 matches)As you can see, it will not make entries for individual ports/protocols; whatever you use as your ACL is what it will match.
Optimize Configuration
Also, note that there is no time limit next to the dynamically created ACL. To add a time limit, we can add it to the dynamic ACL or the auto-command command. The difference between the two is the timeout value on the ACL is absolute, meaning in x minutes, I will terminate the connection. In contrast, the timeout value applied to the access-enable command is an idle timeout value. Here is how to add a 15-minute idle timeout to the access-enable command
PCI-RTR-1(config)# username PCI autocommand access-enable host timeout 15
Now, when we reconnect, this will show up on the ACL
PCI-RTR-1#sh access-list
Extended IP access list LOCKANDKEY
10 permit tcp any host 172.16.25.5 eq telnet (95 matches)
20 deny tcp any host 172.24.24.50 eq telnet
30 Dynamic PCI-ACCESS permit ip any 172.26.45.0 0.0.0.255
permit ip host 10.20.55.24 172.26.45.0 0.0.0.255 (10 matches) (time left 896)
40 deny ip any 172.26.45.0 0.0.0.255 (24 matches)
50 permit ip any any (49 matches)This is a lock and key access-lists in a nutshell. A few more things to make a note of;
- You can only have one dynamic statement per access-list
- When no timeout is configured, entries need to be manually removed
- If you use both the timeout on the ACL and the access-group command, the idle timeout must be less than the absolute timeout (ACL < access-enable timeout)